Amazon Relational Database Service (Amazon RDS) Custom for Oracle is a managed database service for applications that require customization of the underlying operating system and database environment. It provides the benefits of RDS automation with the elevated access needed for legacy, packaged, and custom applications. With Amazon RDS Custom for Oracle, you have the freedom to customize your database and operating system, allowing you to apply special patches and modify database software settings to support third-party applications that necessitate privileged access. By taking advantage of the efficiency of a managed service, you can focus on business-impacting strategic activities.
In this post, we provide guidance on how to deploy Amazon RDS Custom for Oracle using HashiCorp Terraform and the AWS published AWS RDS Custom for Oracle Terraform module. Terraform is an infrastructure as code (IaC) tool that lets you provision resources safely and efficiently. The AWS RDS Custom for Oracle Terraform module (CfO module) provides prescriptive deployment configurations, and automates the deployment and configuration of service required resource types such as AWS Identity and Access Management (IAM) roles, instance profiles, database subnet groups, security groups, and VPC endpoints.
Solution overview
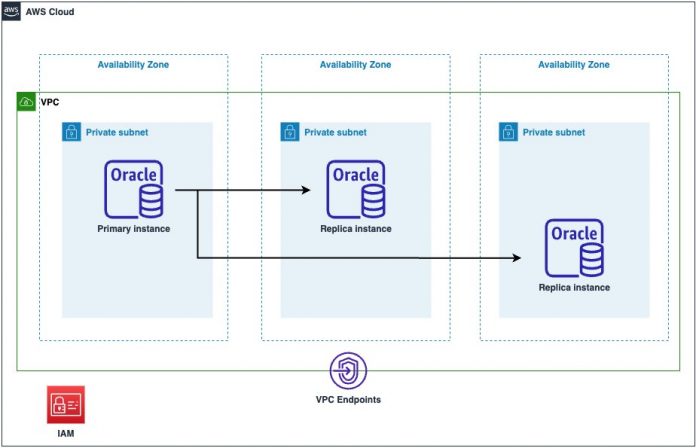
With Terraform and the CfO module, we can automate the creation of an RDS Custom for Oracle primary instance and two read replicas across three Availability Zones, one for the primary instance and two for the replicas. The following diagram illustrates this architecture.
The high-level steps to implement this solution are as follows:
Create and initialize a Terraform project.
Create a customer managed AWS Key Management Service (AWS KMS) key (symmetric).
Create custom engine version (CEV) for Amazon RDS Custom for Oracle.
Create a VPC with three subnets across three Availability Zones.
Create an RDS Custom for Oracle primary instance.
Create two RDS Custom for Oracle read replicas.
Prerequisites
This solution requires the following prerequisites:
Grant required permissions for your IAM user or role
Have Terraform v1.0.0 or newer installed
Create and initialize a Terraform project
For this post, we create a new Terraform project and initialize it. You can work in a local folder of your choosing. Complete the following steps:
In your preferred terminal, create a new folder namedrdscfo:
In your preferred text editor, add a new file with the following Terraform code:
Save the file in the root of the rdscfo folder and name it main.tf.
In your terminal, run the following command to initialize the Terraform working directory:
The output will contain a successful message like the following:
“Terraform has been successfully initialized”
In your terminal, validate the syntax for your Terraform files:
Create a customer managed KMS key
In this step, you use Terraform to create a customer managed key (CMK), which outputs the CMK Amazon Resource Name (ARN). Complete the following steps:
In your text editor, add the following Terraform code to your main.tf file:
Save the file.
In your terminal, apply the Terraform configuration to create the CMK:
Your terminal should have an output similar to the following:
Note the CMK ARN down.
This is required when creating a CEV. In this example, from the preceding output, the CMK ARN is
Create the CEV
CEV creation is not yet supported in Terraform. We use the AWS Management Console to create a CEV. Note that CEV creation can take 2 hours or longer. Complete the following steps:
Create a CEV
When prompted for a KMS key, provide the ARN from the previous section.
Create a VPC with three subnets across three Availability Zones
Next, create the networking resources needed to host your RDS Custom for Oracle instances:
Add the following Terraform code to your main.tf file:
You can change the argument values to your own. We have included comments (starting with #) for most of these arguments with example names for the VPC, CIDR block, and so on:
Save the file.
In your terminal, initialize Terraform again to install the VPC module:
Preview the changes that Terraform intends to make by using the plan command:
Apply the Terraform configuration to create the VPC and subnets:
Create an RDS Custom for Oracle primary instance
You can use Terraform data sources to look up the instance types supported for your custom engine version in the respective operating Region. Use the CfO module (published by AWS) to create an RDS Custom for Oracle primary instance.
Add the following Terraform code to your main.tf file:
You can change the argument values to your own.
Next, you create a primary instance using the CfO module. You can customize the attributes of the module to meet your needs, such as more or less storage and user names and passwords that meet your organization’s security policies.
Edit main.tf to include the module rds_custom_for_oracle with instance parameter values as shown in the following code (you can change the argument values to your own):
Note: You can change argument values with your own. We have included comment (starting with #) for most of these arguments.
Save the file.
In your terminal, initialize Terraform again to install the CfO module:
Preview the changes that Terraform intends to make:
Apply the Terraform configuration to create the RDS CfO primary instance:
Create two RDS Custom for Oracle read replicas
Now you extend the configuration of the CfO module from the previous section to include two read replicas. The CfO module automatically geo-distributes the replicas into separate Availability Zones. You can add the replica configuration using the aws_db_instance_replicas nested block attribute.
Replace the definition of the rds_custom_for_oracle in main.tf with the following code (you can change the argument values to your own):
Preview the changes that Terraform intends to make:
Apply the Terraform configuration to create the RDS CfO replicas:
Clean up
When you no longer need the resources created as part of this post, clean up those resources to save associated costs. You can clean up the AWS resources created in this post using Terraform by using the terraform destroy command.
This will attempt to destroy the CMK created in the first section, but will likely fail because that CMK is associated with a CEV that was created manually using the console. If the terraform destroy command errors, use the console to delete the CEV, and then run the command again.
Conclusion
In this post, we demonstrated how to deploy RDS Custom for Oracle primary and replica instances using Terraform modules. This also involved creating necessary resources like a KMS key, CEV, and VPC.
We recommend testing the modules and given examples in your development environment and making appropriate changes as required to use them in production.
You can find additional Terraform examples on our GitHub repo.
We welcome your feedback. If you have questions or suggestions, leave them in the comments section.
About the Authors
Vishal Patil is a Senior Database Specialist Solutions Architect with Amazon Web Services. Vishal helps customers design architecture, migrate, and optimize Oracle workloads in AWS.
Wesley Hong is a Software Development Manager on the RDS Commercial Engines team.
Tyler Lynch is a Principal Solution Architect at AWS. Tyler supports and contribute to open source software. He is currently in the top 10 contributors of the AWS provider for Terraform, and a Core Contributor for Terraform.
Read MoreAWS Database Blog