Open-source software (OSS) is a type of software that anyone can use, modify and distribute. Development teams can gain tremendous benefits from leveraging the OSS ecosystem, as long as organizations invest in the tooling to address the security, scalability, and sustainability challenges that come with it. Without this tooling, organizations and their software delivery pipelines can continually be exposed to growing cyberattack vectors.
Managing of the open source software lifecycle
Customers can overcome these challenges with Endor Labs.
Wasted engineering cycles: Rather than developing features, engineers often waste precious time chasing false positives reported by current Software Composition Analysis (SCA) tools.
Significant operational risk: Unvalidated, unused, outdated, and unsupported dependencies can impact application resilience, performance, and security.
Lack of inventory and visibility: Inability to answer who is using which open-source software and their dependencies can lead to an incomplete view of direct and transitive dependencies.
Securing software we depend on is a key priority for software supply chain security and something Google Cloud and Endor Labs can help organizations accomplish. With Endor Labs’ Dependency Lifecycle Management solution on Google Cloud, Endor Labs helps security and development teams accelerate development by safely maximizing software reuse.
Securing the software supply chain with Endor Labs Dependency Lifecycle Management
Endor Labs uses program analysis and call graphs to understand how code is actually used in your organization. With an improved understanding of the dependency graph, security and development teams can:
Select dependencies
Secure the software supply chain
Maintain and update OSS safely
Support compliance with emerging U.S. government-led standards and regulation around Software Bill of Materials (SBOM) and the White House Executive Order 14028.
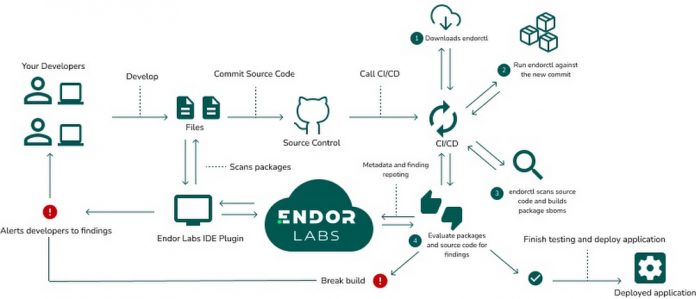
The diagram below illustrates how Endor Labs supports your development lifecycle to help protect your software supply chains — the code, people, systems, and processes that contribute to development and delivery of software.
Organizations run Endor Labs’ client binary called Endorctl in their environment. Endorctl analyzes the source code of their applications. Endorctl reports back metadata of the scanned software packages and repository that is used to display and report on this information.
Users are able to help maintain control of their source code by completing all scanning in their environment and sending back metadata to Endor Labs for processing .
Using the diagram below, let’s take a look at how the process works across different stages:
Developers work on their project and leverage OSS as required for their solution
As part of the CI/CD automation, Endor Labs reviews software packages for dependency usages
Endor labs detects vulnerable dependencies and their reachability, provides visibility to security teams
New findings are reported to stakeholders for remediation using productivity tools within the customer’s enterprise
Architecture overview of Endor Labs using Google Cloud
With Endor Labs running on Google Cloud, the solution is using the following services to provide dependency lifecycle management which can be foundational for supply chain and open source security.
BigQuery is used to retrieve information from datasets, to help identify if an open-source software package has potential typosquatting attacks. BigQuery datasets are also used to provide new dependency information to customers.
Endor Labs uses Google Kubernetes Engine for hosting their services including user interface, API, backend processing for automated scanning infrastructure, and documentation.
Logs from the environment are sent to Cloud Logging for the operational team to monitor and escalate issues for quick resolution.
Endor Labs continuously scans open-source projects and polls GitHub and package repositories for vulnerabilities, which can be leading and lagging indicators of security and operational risk. Customers using the Endor Labs GitHub app are automatically scanned with Kubernetes jobs launched on GKE.
The Endor Labs dependency lifecycle management platform focuses on these outcomes:
Enhance developer productivity by replacing current tools that generate false positive vulnerability alerts due to lack of context on how the OSS code is actually used within your applications.
Improve application performance and minimize attack surface by removing unused dependencies, and selecting sustainable and high-quality dependencies.
Harden software supply chains by identifying risky and unmaintained dependencies to prevent next-generation software supply chain attacks.
Supporting compliance with emerging U.S. government-led standards and regulation around Software Bill of Materials (SBOM) and White House Executive Order 14028.
With Endor Labs’ dependency lifecycle management platform on Google Cloud, you can manage the open-source software lifecycle, helping to accelerate your application development to build robust and secure software.
How Endor Labs works with Google Cloud
Google Cloud is helping technology companies like Endor Labs build innovative applications on Google’s data cloud with simplified access to technology, helpful and dedicated engineering support, and joint go-to-market programs.
They are a member of Google Cloud Partner Advantage program and play an important part in the Google Cloud partner ecosystem. Companies building or integrating solutions on a given platform provides customers with choice and offers more solutions in the market.
To learn more, visit Endor Labs at https://www.endorlabs.com or book a demo or review the reports below.
Cloud BlogRead More