April showers brought a bumper crop of new features. Enterprise Key Management gives the security-conscious complete control over their data. Meanwhile, Environments became available to all customers, managing API authentication got simpler, and more.
Control your own data with Enterprise Key Management
Environments for all
Get all the latest updates from the new Changelog
Simplify API authentication with OpenID Connect
Connect everything
Send files anywhere with custom HTTP
Upload those big files to Autodesk BIM360
Take care of business with Dropbox
Travel through time with Outlook
Control your own data with Enterprise Key Management
Almost all data handled by your organization, including sensitive data like personally-identifying information (PII), financial data, and employee records, passes through your automation platform. No other single app or database handles the same amount and breadth of sensitive information. For example, your HR platform contains all your sensitive employee records, your ERP contains invoicing details, and your CRM contains PII. Data at rest in all of these applications may be encrypted and secure, but if your integration platform isn’t equally secure, all of this data becomes vulnerable, as it is processed. Therefore integration and automation must be a key focus of your data security strategy.
What data needs to be protected?
In Workato, two main types of data need to be protected:
Your job logs, which contain full details of all data processed by Workato within your retention window (30 days for most customers).
Your connections, which store the credentials used to authenticate to your apps.
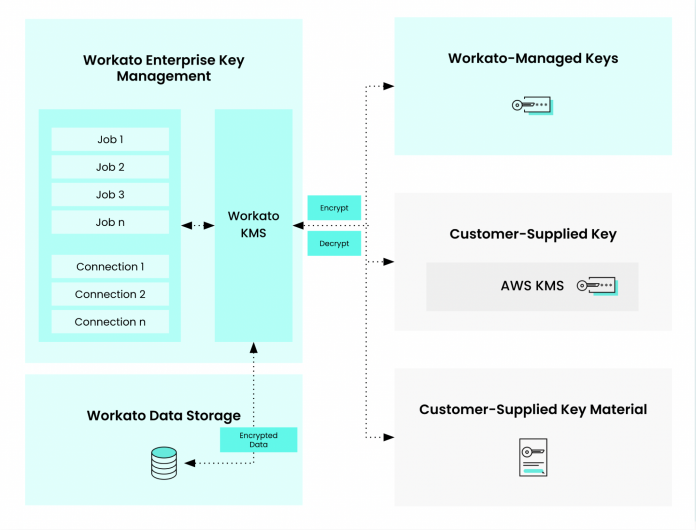
Workato encrypts both types of data under a secure hierarchical key structure. Each Workato workspace has its own dedicated master key, so your data is kept isolated from data in other workspaces.
Protecting data with a Key Management System
While security is important for everyone, companies in highly-regulated industries, like healthcare and financial services, often have very specific security requirements. To meet these requirements, you may need to implement an org-wide key management system (KMS), through a cloud provider like AWS KMS.
A KMS helps you to manage all of the encryption keys used across the org, including for your various cloud platforms. It also allows for regular rotation of keys, to limit the amount of time any one key is in use, and for instant revocation of access to keys in response to any security incidents. Implementing a KMS helps to ensure the security and integrity of all your data.
Now, with the release of Enterprise Key Management, Workato is becoming the only enterprise automation platform to give you control over your own master encryption key.
Advantages of controlling your own encryption key
Revoke access instantly
Because you control your key, you can revoke access to it at any time. Without access to your master key. Neither Workato, nor any of your Workato users, can access any of your stored data. You can revoke access permanently, by deleting your master key. You can also revoke access temporarily, either by disabling the key, or by updating your access policy to deny access to Workato.
Conform to security policies
Your organization’s internal security policies may require you to centrally manage the keys you use on all vendor platforms. Controlling your own master key also means that you can set up AWS KMS to automatically rotate key material at whatever interval is required by your policy.
How it works
With Enterprise Key Management, you can maintain your own encryption key in a service like AWS Key Management Service (KMS) and create an access policy granting Workato access to the key. Workato uses your own encryption key to encrypt other keys in the hierarchy.
With your master encryption key under your own control in AWS KMS, you can respond to potential threats in a number of ways:
Issue new keys
When you issue a new master key with a new key ID, Workato will automatically re-encrypt all stored data using the new master key. Some organizations will do this at regular intervals, in addition to rotating key material. This will not cause any disruption to your implementation of Workato. User access will not be interrupted and jobs will be processed as normal.
Disable or revoke access to your master key
You can temporarily revoke access to your data by disabling your master key, or updating your access policy to deny access to Workato. This action will make all job and connection data stored by Workato inaccessible. Workato users will not be able to see stored job data, or update connections to any of your apps. No data can be processed or sent from Workato and any new jobs will fail, until you create new keys. When you restore access you may need to manually re-authenticate connections to your apps.
Delete your master key
Deleting your master key will make all job and connection data stored by Workato permanently inaccessible. Workato users will not be able to see stored job data, or authenticate connections to any of your apps. No data can be processed or sent from Workato and any new jobs will fail. While past data will not be recoverable, all of your recipes, connections, account properties, lookup tables and other assets will remain active. When you issue new keys, you will be able to re-authenticate your connections and begin to process new jobs.
To learn more about Enterprise Key Management, and about how your data in Workato is already protected, read the full launch blog.
Environments for all
Late last year, we released Environments–a new way to manage change in Workato–for new workspaces. We’re now excited to announce that existing customers can now begin adding Environments to existing workspaces. Brush up on what you can do with Environments below, or check out the full blog for more detail.
Change management for the low-code/no-code world
Environments are the simple, safe way to manage change to your automations in Workato. Each workspace includes three environments:
Development – to experiment, build, test and debug
Test – for quality assurance and user acceptance testing
Production – when your project is tested and ready to roll, deploy it seamlessly to your production environment.
Protect your production automations with role-based access control
As a best practice for change management, you should limit the ability to make changes in your production environment only to those who are responsible for it. Workato’s role-based access control feature allows you to control access to each project, and to each environment. For example, an integration builder might have full access in a development environment, but only read access in production to enable troubleshooting.
Deploy projects between environments
Deploying a project is simple. No scripts, no external tools, no JSON manifests. Just head to the Deployments tab and click Deploy project. The deployment wizard detects and includes all dependencies and automatically builds a customizable deployment package for you.
Auditability and instant rollbacks
At any time, view a complete deployment history for a project in the Deployments tab. You can see who deployed a project, to which environment, and why. You can also download any deployment as a JSON package if you need all the details.
Sometimes accidents happen, even with the best processes. If a change to your project causes an unexpected problem, don’t panic. You can roll back to a previous stable deployment from your deployment log at any time.
How to get started
Reach out to your Customer Success Manager to get started on migrating to environments.
Get all the latest updates from the new Changelog
Look, we get it, there’s a lot going on. You can’t spend all your time keeping up with new Workato features, even if you’re as excited about them as we are. If you ever want to catch up with what’s been happening here, just head over to our new Changelog.
The Changelog lists every major Workato update. You can filter by product category, search by keyword, or look at a particular year or quarter. Now that you’re caught up on what we’ve been doing, what’s new with you?
Simplify API authentication with OpenID Connect
Workato’s API platform makes it easy to build and deploy enterprise APIs, and slashes the ops burden that comes with traditional API management. For example, you can create API clients, assign them access profiles and generate credentials all from Workato, with no need to deal with a complex IAM system. The API platform supports most common authentication frameworks, from a simple access token, to Oauth 2.0.
However, many organizations already use an Identity platform (IDP), such as Okta, or OneLogin, to manage all employee access to internal systems. If your org uses an IDP platform, you might want to leverage it to manage access to the APIs you build in Workato. Well, now you can, with the help of OpenID Connect, a standard protocol to manage authentication and trust across domains. Most major IDPs support OpenID Connect, including Okta, OneLogin, Auth0, and others.
When using OpenID Connect to manage API access:
You don’t need to generate credentials in Workato or share them manually.
You can use the roles and groups you’ve already defined in your IDP to govern access to your APIs.
Your users don’t need to manage additional credentials just to access Workato APIs.
You can take advantage of your IDPs signing key rotation feature. Workato will automatically detect changes and update the signing key with zero downtime.
To learn how to set up OpenID Connect for Workato APIs, check out the docs
Connect Everything
Send files anywhere with custom HTTP
We’ve added support for multipart form data to the custom HTTP connector. This type of request is often used to send files and other data in the same request. For example, a document image paired with an ID.
When setting up your custom HTTP request, just select Multipart form as the request content type.
If you need to upload a file as part of the request, when setting up your schema, select Yes, under File Attachment.
Then, just set the file content and file name in the recipe builder. You can set static values or map the appropriate datapills.
Upload those big files to Autodesk BIM360
Okay, your files are big, quit bragging. To support bulk data uploads into BIM360 we’ve reinforced the upload files action to support upload of files up to 15GB.
We’ve also added a more precise trigger for monitoring new or updated documents. You can now watch for documents only within a particular project folder, or its subfolders.
Take care of business with Dropbox
The Dropbox connector now supports Business Folders for all actions. When you set up your connection, the folder selection dropdown will show both personal and business folders.
And if you have a lot of folders to select from, the dropdown now supports up to 2000 folders. Use the search box to help you find the right folder fast.
Travel through time with Outlook
Teams are more distributed than ever before, which means considering timezones when managing calendar events. When creating or updating an event in Workato, you can now specify a timezone.
In addition, when creating an event, you can now set a custom transaction ID for event tracking and classification. The ID helps to prevent duplicate event creation and will be available when you search, get, update or list events.
The post Product Scoop – April 2022 appeared first on Workato Product Hub.
Read MoreWorkato Product Hub