Encryption is a fundamental control for data security, sovereignty, and privacy in the cloud. While Google Cloud provides default encryption for customer data at rest, many organizations want greater control over their encryption keys that control access to their data.
Customer-Managed Encryption Keys (CMEK) can help you by providing flexibility in cryptographic key creation, rotation, usage logging, and storage.While CMEK provides the additional control that many organizations need, using it requires manual processes that require time and effort to ensure that the desired controls and configurations are implemented.
To help make CMEK configuration more efficient, today, we’re excited to announce the launch of Cloud KMS Autokey in preview. Cloud KMS Autokey automates key control operations for CMEK. It incorporates recommended practices that can significantly reduce the toil associated with managing your own encryption keys, which can help developers complete their projects faster.
Cloud KMS Autokey eliminates manual effort in key creation. Keyrings and keys are generated automatically during resource creation, and the necessary IAM roles for encryption and decryption operations are assigned at the same time. Autokey also simplifies key selection by automatically choosing the appropriate key type for each resource, reducing complexity and manual effort.
Here’s how it works
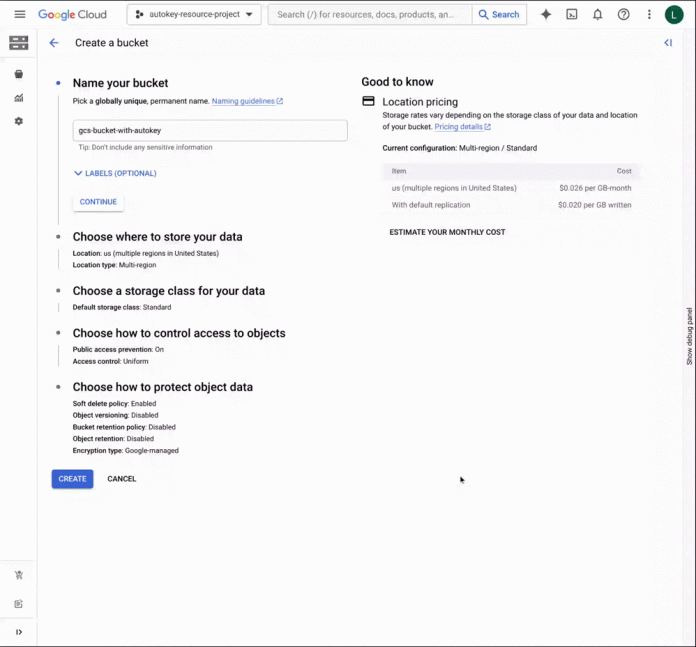
Let’s say you’ve been tasked with a project that requires you to create a Google Cloud storage bucket, Compute Engine instances with persistent disks, and a BigQuery dataset. The data in each of these services needs to be encrypted with a key that you control. From the control panel, you can now select “Cloud KMS with Autokey” when configuring encryption for these resources.
Creating a Google Cloud Storage bucket using a key created with KMS Autokey.
Creating a Google Cloud Persistent Disk using a key created with KMS Autokey.
Creating a BigQuery dataset using a key created with KMS Autokey.
When you request your key, Cloud KMS Autokey automatically creates a key ring with your new encryption key in the same location as your resource if a key ring for that project and location doesn’t already exist.
For example, if you created the resource in us-central1, then KMS Autokey creates the key ring in us-central1.
Cloud KMS Autokey automatically creates a keyring with your new key
You can monitor and maintain keys created by Cloud KMS Autokey the same way as you do for any other Cloud KMS key.
When you create encryption keys with Cloud KMS Autokey, you’re helping to accomplish three vital goals when implementing CMEK:
Ensuring consistent practices: When you request a key, the Cloud KMS Autokey service account automatically generates keys in accordance with the recommendations embedded within Cloud KMS Autokey.
Creating granular encryption keys: A new key is created with a granularity appropriate to each resource type, giving you greater control over operations like crypto-shredding if you need to disable or delete a key without affecting multiple protected resources
Increasing your productivity: You quickly create CMEK-protected resources, without the back-and-forth operational toil of a developer requesting new keys from another team
Getting started
You can enable Cloud KMS Autokey at the resource folder level. Developers working in projects in that folder will be able to access Autokey. The KMS Admin will not need to do any pre-planning or key creation for those projects.
Authorized users can request a cryptographic key directly from the Cloud KMS Autokey service account while preserving separation of duties. As an authorized user, Terraform and other infrastructure-as-code processes no longer need to run with elevated key-creation privileges, which can help reduce your attack surface. Instead, the Terraform code creates a key handle and uses the returned key to protect the resource.
After setup, Cloud KMS Autokey acts like a key-managing assistant. It can:
Create a key ring for the location, if a key ring doesn’t already exist.
Create a key with the appropriate granularity and location for the resource type, if that key doesn’t already exist, in accordance with the recommendations embedded within Cloud KMS Autokey.
Create the service agent in the project where resources will be encrypted, if it doesn’t already exist.
Give the service agent encrypt and decrypt authority on the key.
Administrators can continue to monitor all keys created and used through the Cloud KMS Dashboard and Key Usage Tracking feature.
Try it out
Cloud KMS Autokey can be used via the Google Cloud Console, Cloud KMS API, and Terraform. For more information and if you have questions, please review our documentation.
Cloud BlogRead More