In this post, we explain how to migrate the logins, database roles, users, and object-level permissions from on-prem or Amazon Elastic Compute Cloud (Amazon EC2) for SQL Server to Amazon Relational Database Service (Amazon RDS) for SQL Server using the T-SQL.
When it comes to gaining access to SQL Server, there is a need for an SQL Login which is used for authentication and a database user which is used for authorization. Authentication checks whether you have permission to log in to a system, whereas authorization specifies what you can do once connected. In Microsoft SQL Server, a login is created at the instance level, and a user is created at the database level. Logins can be local SQL Server users or Windows users or groups, including Active Directory users or groups.
When you use SQL Server native backup and restore to migrate an SQL Server Instance along with your databases, everything is migrated, including the username and permissions.
In some of the migration scenarios where native backup and restore is not used as the migration option, when you move one or more selected databases from one SQL Server instance to another, logins and users’ permissions of the objects in the databases are not migrated. Also in the scenarios, when there are requirements to create a database at the destination side in advance, you must migrate logins with passwords and users with object-level permissions from one SQL Server instance to another separately. With that the application can seamlessly access new target databases and objects, with the same permissions as source without a break.
Use Cases
AWS DMS with a full load for homogenous migrations.
Migrating the databases from the SQL Server instance on server A to the instance on server B.
Solution Overview
For the scenarios where logins and users permissions are not migrated, we generate dynamic T-SQL scripts to create the logins, roles, users and object-level permissions for single and multiple databases.
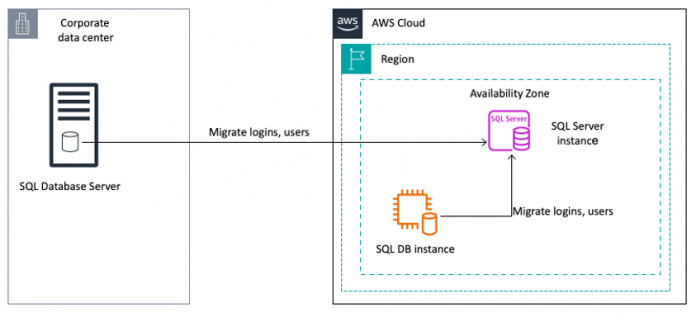
The following diagram illustrates the high-level architecture of migrating logins and database users from on-premises or Amazon EC2 for SQL Server to Amazon RDS for SQL Server.
Prerequisites
To get started, you need to have the following setup
An on-premises SQL Server instance or Amazon EC2 for SQL Server instance
An Amazon RDS for SQL Server DB instance (Single-AZ or Multi-AZ)
Connectivity between an on-premise SQL Server or SQL Server on Amazon EC2 for SQL Server and Amazon RDS for SQL Server
In a source server, a login that is part of an ALTER ANY LOGIN server level securable permission can run the statement from the sys.server_principals and sys.server_permissions.
A target Amazon RDS for SQL Server database with required user-defined objects (tables, views, functions, and stored procedures) and a db_owner with the required permissions to create objects in SQL Server database
A login that is part of processadmin, public, and setupadmin fixed server roles in Amazon RDS for SQL Server instance.
1. Migrate SQL Server Logins, server roles and Server level grant permissions to Amazon RDS for SQL Server
To migrate the logins from SQL Server running on EC2 or on-premises to Amazon RDS for SQL Server, run the following steps to script out the create login scripts with a hash password with SID. The output script generates the create login script with password hash and SID.
Migrate logins
This section explains how to generate the create logins script from a source SQL Server instance and migrate it to the target Amazon RDS for SQL Server.
Connect to your source SQL Server instance (Amazon EC2 or On-premises) as a local administrator using Remote Desktop Protocol (RDP).
Connect to the SQL Server instance using SQL Server Manager Studio (SSMS)
In the SSMS query editor, select the Results to Grid (selecting Ctrl + D) option
Run the following script from the new query window to generate the create login script. The output of the query provides the logins creation script.
Note:
You can ignore the SQL Server Reporting Services (SSRS) related service account logins as they need to be handled in a different way in Amazon RDS for SQL Server. For configuring SSRS in Amazon RDS for SQL Server, refer to Support for SQL Server Reporting Services in Amazon RDS for SQL Server.
Exclude any other logins not required on target Amazon RDS for SQL Server.
Connect to the target Amazon RDS for SQL Server using SQL Server Manager Studio (SSMS) and copy the required logins script, generated in step 4.
Note: Be responsible and cautious while copying the output and pasting it at the target database, as it contains sensitive data.
Run the copied script using the RDS master user or a login with “Alter any login” server level securable that is part of a processadmin, and setupadmin fixed server roles (refer the section: Microsoft SQL Server Security) in Amazon RDS for SQL Server instance.
Validate the script execution output for any errors.
After the successful migration of logins, continue with the server role membership migration.
Migrate server role membership
This section explains how to generate the create server role membership script from a source SQL Server instance and migrate it to the target Amazon RDS for SQL Server.
Connect to your source SQL Server instance (Amazon EC2 or On-premises) as a local administrator using Remote Desktop Protocol (RDP).
Connect to the SQL Server instance using SQL Server Manager Studio (SSMS)
In the SSMS query editor, select the Results to Grid (selecting Ctrl + D) option
Run the following script from the new query window to generate the server role membership script. The output of the query provides the server role membership creation script.
Connect to the target Amazon RDS for SQL Server using SQL Server Manager Studio (SSMS) and copy the required logins script, generated in step 4.
Run the copied script using the RDS master user or a login with “Alter any login” server level securable that is part of a processadmin, and setupadmin fixed server roles(refer the section: Microsoft SQL Server Security) in Amazon RDS for SQL Server instance.
Note: With Amazon RDS for SQL Server level permissions limitations, an user can only grant “setupadmin”, “processadmin” server level roles for logins or groups.
Validate the script execution output for any errors.
After the successful migration of the server role membership, continue with the server level grant permission migration.
Migrate server level grant permissions
This section explains how to generate the create server level grant permissions script from the source SQL Server instance and migrate it to the target Amazon RDS for SQL Server.
Connect to your source SQL Server instance (Amazon EC2 or On-premises) as a local administrator using Remote Desktop Protocol (RDP).
Connect to the SQL Server instance using SQL Server Manager Studio (SSMS)
In the SSMS query editor, select the Results to Grid (selecting Ctrl + D) option
Run the following script from the new query window to generate the create login script. The output of the query provides the server level grant permissions creation script.
Connect to the target Amazon RDS for SQL Server using SQL Server Manager Studio (SSMS) and copy the required logins script, generated in step 4.
Run the copied script using the RDS master user or a login with “Alter any login” server level securable that is part of a processadmin, and setupadmin fixed server roles(refer the section: Microsoft SQL Server Security) in Amazon RDS for SQL Server instance.
Validate the script execution output for any errors.
2. Migrate SQL Server database users, roles and object-level permissions to Amazon RDS for SQL Server
To migrate the database users, roles and object-level permissions from Amazon EC2 for SQL Server or on-premises to Amazon RDS for SQL Server, complete the following steps to script out the create users, roles and object-level permission scripts.
Migrate database users, roles, role membership and object-level permissions for single or multiple databases.
For a Single Database
This section explains how to generate the users, roles, role membership and object-level permissions for a single database using the T-SQL script from a source SQL server instance and migrate to target Amazon RDS for SQL Server.
Connect to your source SQL Server instance (Amazon EC2 or On-premises) as a local administrator using Remote Desktop Protocol (RDP).
Connect to SQL Server instance using SQL Server Manager Studio (SSMS)
In the SSMS query editor, select the Results to Text (selecting Ctrl + T) option
Run the following script from the new query window to generate the users, roles, role membership and object-level permissions create script.
Note: Make sure the script is executed for the <database_name>.
Connect to the target Amazon RDS for SQL Server using SQL Server Manager Studio (SSMS) and copy the output scripts generated in step 4.
Run the copied script using a login that is part of a db_owner role for that database in the Amazon RDS for SQL Server instance.
Validate the script execution output for any errors.
For Multiple User Databases
This section explains how to generate the users, roles, role membership and object-level permissions for multiple user-defined databases using T-SQL script from source SQL server instance and migrate to target Amazon RDS for SQL Server.
Connect to your source SQL Server instance (Amazon EC2 or On-premises) as a local administrator using Remote Desktop Protocol (RDP).
Connect to the SQL Server instance using SQL Server Manager Studio (SSMS)
In the SSMS query editor, select the Results to Text (selecting Ctrl + T) option
Run the following script from the new query window to generate the users, roles, role membership and object-level permissions create script
Connect to the target Amazon RDS for SQL Server using SQL Server Manager Studio (SSMS) and copy the output scripts generated in step 4.
Run the copied script using a login that is part of a db_owner role for that database in the Amazon RDS for SQL Server instance.
Validate the script execution output for any errors
Migrate sysadmin logins as db_owner in Amazon RDS for SQL Server
As per Amazon RDS for SQL Server level permission limitations, we cannot grant sysadmin privileges to the users at the target. In the case of granting db_owner permission to the source sysadmin users for user-defined databases, run the following script.
Clean up the environment
To avoid future charges, remove all of the components created while testing this use case by completing the following steps:
On the Amazon RDS console, choose Databases in the navigation pane.
Select the databases you set up and on the Actions menu, choose Delete.
Enter delete me to confirm deletion.
For more information about deleting an instance, refer to Deleting a DB instance.
On the Amazon EC2 console, locate the SQL Server on Amazon EC2 instance that you used as your source and delete the instance.
Conclusion
In this post, we described how to migrate the logins, database roles, users and object-level permissions to Amazon RDS for SQL Server using T-SQL. Give it a try, and let us know what you think by commenting on this post. We’re always looking forward to your feedback, either through your usual AWS support contacts, or on the AWS Forum for Amazon RDS.
About the authors
Ramesh Babu Donti, a Lead Database Consultant with AWS Professional Services based out of Hyderabad, India. He focuses on helping customers to build high-available, cost-effective database solutions and migrate their large scale databases to AWS.
Sai Krishna Namburu, a Lead Database Consultant with AWS Professional Services based out of Hyderabad, India. With good knowledge on relational databases adding hands-on in homogenous and heterogenous database migrations, he helps the customer’s migration to AWS cloud and their optimisations.
Jinesh Shah, a Database Consultant with AWS Professional Services, based in Texas, USA. He works with customers in their journey to the cloud and helps them successfully achieve cost-effective, scalable, optimized, secure and highly-available database migration and modernization solutions.
Indu Shekhar, a Database Consultant with AWS Professional Services based out of Hyderabad, India.With good knowledge on relational databases adding hands-on in homogenous and heterogenous database migrations, helps customers in migrating to AWS cloud and their optimisations.
Read MoreAWS Database Blog