With the announcement that Amazon Relational Database Service (Amazon RDS) for Oracle now supports integration with Amazon Elastic File System (Amazon EFS), you can keep temporary files like Oracle Data Pump export, import files on Amazon EFS file system, and directly access from it. Furthermore, you can leverage Amazon EFS integration for sharing a file system between Amazon RDS for Oracle DB instance and an application instance or across multiple Amazon RDS for Oracle DB instances to address your application architecture needs.
In the first post in this two-part series, we explained the benefits of using Amazon RDS for Oracle and Amazon EFS integration, detailed setup instructions, and the various use cases.
In this post, we discuss the importance of strengthening Amazon EFS access with file system policy and enforcing encryption in transit along with the detailed implementation steps.
Securing the file system access and network traffic
Amazon EFS integration with Amazon RDS for Oracle works with the default (empty) Amazon EFS file system policy. The default policy doesn’t use AWS Identity and Access Management (IAM) to authenticate. Instead, it grants full access to any anonymous client that can connect to the file system using a mount target. The default policy is in effect whenever a user-configured file system policy isn’t in effect, including at file system creation.
To strengthen access to your Amazon EFS file system for all clients, including Amazon RDS for Oracle, you can configure IAM permissions using resource policy. When a client connects to a file system, Amazon EFS evaluates the file system’s IAM resource policy, which is called a file system policy, along with any identity-based IAM policies, to determine the appropriate file system access permissions to grant.
In addition to this, using predefined condition keys in the policy, you can enforce the encryption-in-transit using Transport Layer Security 1.2 (TLS) with an industry-standard AES-256 cipher to secure the traffic between the file system and clients.
In the following sections, we walk you through the steps to integrate Amazon EFS file system with Amazon RDS for Oracle using the file system policy that controls access to specific clients and enforce TLS encryption.
Prerequisites
Before we begin, we assume that you have the following prerequisites.
An Amazon RDS for Oracle database version 19c July 2022 Release Update or later with Enterprise or Standard Edition 2 (SE2). Refer to Creating an Amazon RDS DB instance.
An Amazon Elastic Compute Cloud (Amazon EC2) instance with Amazon Linux 2 AMI or with one of the Linux distributions listed in AWS Documentation that supports Amazon EFS mount helper.
AWS Key Management Service (AWS KMS) key to encrypt the Amazon EFS data at rest. If you already have a key used for RDS encryption, you can reuse it.
Because this solution involves AWS resource setup and utilization, it will incur costs on your account. Refer to AWS Pricing for more information.
Create IAM roles for Amazon RDS and Amazon EC2
Your first step is to create IAM roles for Amazon RDS and Amazon EC2.
On the IAM console, choose Roles in the left panel and click Create role.
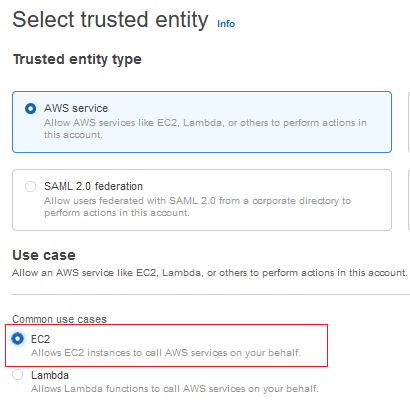
Select Trusted entity type as AWS service.
Select Use case as EC2 and choose Next.
Don’t add any permissions or policies. Choose Next
Enter a Role name and Description for the role and choose Create role.
Create another role for Amazon RDS.
Select Trusted entity type as AWS service.
Select Use case as RDS – Add Role to Database and choose Next.
Don’t add any permissions or policies. Choose Next.
Enter a Role name and Description for the Amazon RDS role and choose Create role.
Create Amazon EFS file system
Now you create an Amazon EFS file system and mount targets.
On the Amazon EFS console, choose Create file system.
Enter a Name for EFS.
Select the Virtual Private Cloud (VPC).
Select Storage class as Standard and choose Customize.
Select the Enable encryption of data at rest check box and choose the KMS key from the dropdown and choose Next.
Select the subnet where you want to place this file system.
Select the security groups that are attached to your EC2 instance and RDS database mentioned in the prerequisites. Choose Next.
Don’t add any file system policy now. Choose Next and Create file system.
Prepare and add the file system policy
In this section, you prepare a filesystem policy and attach to Amazon EFS file system to limit the client access and enforce encryption-in-transit.
In the following example policy, replace the Region, account ID, and file system ID to prepare the policy.
In the Amazon EFS console, select the file system created earlier, choose the File system policy tab, and choose Edit.
Select the right-side Policy editor {JSON} panel and paste the policy prepared in the previous step and choose Save.
Update security group rules
In this section, you add security group rules to allow access among Amazon EFS filesystem, Amazon EC2 instance, and Amazon RDS for Oracle instance.
From the Amazon EC2 console, click Security Groups from the left panel.
Select the security group that is attached to the Amazon EC2 instance. Edit the inbound rules and add the inbound rule for NFS with the same source as the security group name.
From the Amazon EC2 console, choose Security Groups from the left panel.
Select the security group that is attached to the Amazon RDS instance. Edit the inbound rules and add the inbound rule for NFS with the same source as the security group name.
Both the Amazon EC2 and Amazon RDS security groups will have the following default outbound rule.
Add IAM role to Amazon EC2 instance
Now you add IAM role that was created earlier for EC2 to Amazon EC2 instance.
In the Amazon EC2 console, select your Amazon EC2 instance.
From the Actions menu, choose Security and then Modify IAM role.
Select the IAM role from the dropdown that was created earlier for EC2 and choose Update IAM role.
Mount the file system
In this section, you mount the file system and setup permission for Amazon RDS instance access.
Log in to the Amazon EC2 instance and create a directory to mount the EFS.
Mount the file system as shown in the following command, replace the file system ID that you have created.
Note: If you get an error such as unknown filesystem type ‘efs’, then ensure amazon-efs-utils is installed. Refer to Amazon EFS User Guide for installation steps.
Verify the file system mounted.
Create a subdirectory inside the file system mount directory.
Change the permissions so that the RDS instance can access this because the user for the Amazon RDS for Oracle instance is in the ‘others’ category.
Create option group
In this section, you create an option group and add option along with file system details.
In the Amazon RDS console, choose Options groups in the left panel.
Choose Create group and enter the Name, Engine, and Major Engine Version details according to your Amazon RDS for Oracle database and choose Create.
Select the option group created in the previous step and choose Add option.
Choose Option name as EFS_INTEGRATION.
Enter the EFS_ID that you created earlier.
Enter TRUE for USE_IAM_ROLE and choose Add option.
Attach IAM role to the RDS instance
Now you add IAM role that was created earlier for RDS to Amazon RDS instance.
From the Amazon RDS console, choose Databases in the navigation pane.
Select your RDS instance and scroll down to Manage IAM roles.
From the dropdown, select the IAM role that you have created earlier for Amazon RDS.
Select the Feature as EFS_INTEGRATION and choose Add role.
Wait for the role to show Status as Active
Modify the RDS instance and Add option group
In this section, you modify Amazon RDS instance and select the option group that was created earlier with EFS integration option.
From the Amazon RDS console, choose Databases in the navigation pane.
Select your RDS instance and choose Modify.
Scroll down to Additional configuration and select the Option group that you created from the dropdown and choose Continue.
Verify the summary of modifications, select Apply immediately, and choose Modify DB instance.
After the Amazon RDS instance status shows Available, select the instance and go to Configuration tab and verify the Option groups shows in-sync
Verify integration between Amazon RDS and Amazon EFS
Now you verify the Amazon EFS integration by creating a directory and writing a test file from Amazon RDS instance.
Log in to the Amazon RDS for Oracle instance as an admin user.
Create Oracle directory pointing to the Amazon EFS file system as shown in the following command.
Replace the file system ID and the subdirectory name. Retain the prefix /rdsefs-
Run the following procedure and check if Amazon RDS is able to write files to Amazon EFS.
Log in to the Amazon EC2 instance and check if the test file is written by the Amazon RDS instance.
In case of any issues, refer to the Troubleshooting Amazon EFS integration section from the Amazon EFS User Guide and take necessary action. With this integration, this Oracle directory can be used in data pump jobs and RMAN tasks in the Oracle RDS instance, which provides direct access to the EFS file system.
Limitations
Review the requirements and restrictions listed in Amazon EFS integration while evaluating this implementation. In addition to this, you must use the EFS mount helper to mount your Amazon EFS file systems in order to use IAM authorization to control client access.
Cleanup
To avoid future charges and remove all the resources used while testing this use case, complete the following steps.
On the Amazon RDS console, select your db instance and delete, refer to Deleting a DB instance.
On the Amazon EC2 console, select your EC2 instance and delete the instance.
On the Amazon EFS console, select your file system and delete the file system.
Conclusion
In this post, we discussed the implementation steps to integrate Amazon EFS with Amazon RDS for Oracle database with fine-grained access control using file system policy and enhanced security by enforcing encryption in transit. For more details about this feature, refer to Amazon RDS for Oracle Integration with Amazon EFS.
If you have any questions, comments, or suggestions, leave a comment.
About the Authors
Gokul Gunasekaran is a Consultant with the Professional Services team at Amazon Web Services. He works as a Database Migration Specialist to help AWS customers migrate and modernize their on-premises database workloads to AWS cloud database solutions.
Puja Audhya is a Consultant with Database Migration and Modernization team at Amazon Web Services. She helps AWS Customers migrate the databases to AWS cloud database services.
Neha Sharma is a Database Consultant with Amazon Web Services. With over a decade of experience in working with databases, she enables AWS customers to migrate their databases to AWS Cloud. Besides work, she likes to be actively involved in various sports activities and likes to socialize with people.
Read MoreAWS Database Blog