Many organizations around the world, such as government agencies, financial institutions, and non-profits, are looking for ways to protect their valuable data from ransomware attacks and natural disasters. In addition, many businesses are required to maintain their data long term to meet regulatory compliance and business policies.
In the cloud, a strategy we see customers employ to accomplish the goal of protecting their data is to create a centralized account to which multiple departments or lines of business within the organization can back up their data. Backing up to a different account can offer protection if your production account is compromised by a ransomware attack, for example. Furthermore, organizations often copy their data to another geographic region as a method of complementing their disaster recovery (DR) strategy, thereby offering additional protection in case of a complete regional failure. A backup and restore-based DR solution is economical when the requirements for recovery point objective (RPO) and recovery time objective (RTO) are in the order of hours.
In the AWS Cloud, you can use AWS Backup along with AWS Organizations to centrally deploy, manage, and monitor data protection policies across multiple accounts and organizational units. AWS Backup offers a cost-effective, fully managed, policy-based service that simplifies data protection at scale, and can help you support regulatory compliance obligations and meet your business continuity goals. AWS Backup supports a number of AWS services, including Amazon Relational Database Service (Amazon RDS) and Amazon Aurora.
In this post, we discuss how you can use AWS Backup to automate copying your RDS database snapshots from one AWS account to another AWS account in the same AWS Region, and to copy the backup to a different Region in the destination account. We also show how you can restore the database using a cross-account snapshot backup.
Solution overview
Amazon RDS and Amazon Aurora support cross-Region backups, or cross-account backups, but not both in the same backup plan. The code provided in this post creates an Amazon EventBridge rule and AWS Lambda function to accomplish both.
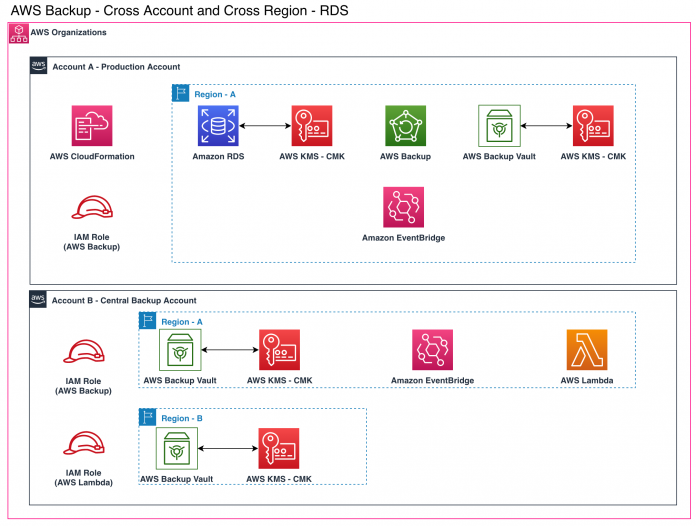
The following diagram illustrates the high-level architecture of the solution.
As illustrated in the diagram, the RDS instance in the Production account (A) in Region A is backed up by AWS Backup, and then that backup is copied to the Central Backup account (B) in Region A to achieve the cross-account backup copy.
After the copy job is complete, an EventBridge rule in the Production account (Region A) forwards the “copy job complete” notification to the Central Backup account (Region A) event bus.
In the Central Backup account (Region A), an EventBridge rule identifies the incoming event from the Production account and triggers a Lambda function that requests AWS Backup to copy the backup from Region A to Region B to achieve the cross-Region backup copy within the Central Backup account.
At a high level, the following steps are involved in setting up cross-account backups between accounts in your organization. As part of this post, we provide you with an AWS CloudFormation template that accomplishes Steps 1–6. We also provide steps to restore the database in the Central Backup account from a snapshot.
Create an AWS Key Management Service (AWS KMS) customer managed key (CMK) in the Production and Central Backup account. The keys are used by the AWS Backup vault in each account.
Create an AWS Backup vault in each account and assign the previously created KMS CMK to each vault.
Create a backup plan in the Production account that creates a snapshot of the database on a predefined schedule and copies the resulting snapshot to the Central Backup account.
Create a Lambda function in the Central Backup account to copy the snapshot to a different Region.
Create an EventBridge rule in the Production account to forward the event notifications of AWS Backup copy completion to the Central Backup account.
Create EventBridge rules in the Central Backup account to trigger the Lambda function that copies the incoming backup into another Region.
Use the snapshot backup to restore the RDS database in the Central Backup account.
Prerequisites
The following are the prerequisites for implementing the solution:
An AWS Identity and Management (IAM) account with administrator privileges for the services used in this solution
An existing organization structure configured in AWS Organizations
Opting in for backing up the appropriate services, Amazon RDS in this case, in each Region that you want to use AWS Backup to manage backups
An Amazon RDS for Oracle database
Additionally, we assume that you’re familiar with the following services:
AWS Backup
AWS CloudFormation
Amazon EventBridge
Amazon RDS
AWS KMS
AWS Lambda
Keep in mind the following:
We use an Amazon RDS for Oracle database in this post but you can use the same solution with other RDS engines and even with Amazon Aurora.
Backups managed by AWS Backup are considered manual DB snapshots, and don’t count toward the DB snapshot quota for Amazon RDS
Cross-account backups aren’t possible for RDS databases encrypted using the default KMS key for Amazon RDS because the default service key can’t be shared with other accounts
If the RDS database is encrypted with a CMK, the CMK should be shared with all accounts to which the snapshot is to be copied
You can’t share a database snapshot that uses an option group with permanent or persistent options, except for Oracle database instances that have the Timezone or OLS option (or both)
For more information about sharing snapshots, see Sharing a DB snapshot.
Implement the solution
For this post, we set up an organizational structure that has three accounts. For more information about setting up AWS Organizations, see Getting Started with AWS Organizations.
Next, validate that cross-account backups have been enabled in AWS Backup in the management account. You must also validate that you have opted in for backing up Amazon RDS in each Region where you want to use AWS Backup. To validate this, log in to each account, navigate to the AWS Backup console, and choose the appropriate settings under My Account.
The following screenshot is an example of AWS Backup settings in the management account.
Now that the prerequisites are verified, let’s begin configuring cross-account backups.
Before you start, make a note of the following information and download the CloudFormation templates:
AWS account ID of the Central Backup account
Organizations ID
AWS CloudFormation is a free service; however, you’re charged for the AWS resources you create with your stacks at the current rates.
Run the CloudFormation stack in the Production account (Region A)
In this section, you create a CloudFormation stack in the Production account where the RDS database resides. The stack creates the following resources:
IAM role required by AWS Backup
AWS Backup vault and KMS CMK for vault encryption
AWS Backup plan
IAM policy and role for EventBridge and a rule to forward the copy complete notifications to the Central Backup account
Sign in to the AWS Management Console in the Production account.
Confirm the Region you’re working in (referred to as Region A in this post).
Search for CloudFormation or, on the Services menu, choose CloudFormation under Management & Governance.
If this is the first CloudFormation stack you’re creating and you’re redirected to the AWS CloudFormation welcome screen, choose Create Stack to go directly to the window for specifying the CloudFormation template (see Step 5).
On the Create stack menu, choose With new resources.
For Template source, select Upload a template file.
Choose Choose file and upload account_a_region_a.yml from the files you downloaded.
Choose Next.
Under Specify stack details, provide a value for each parameter listed in the following table.
Parameter Name
Value Example
Stack Name
aws-backup-rds-stack
AWS Backup IAM Role Name
aws-backup-role
AWS Backup Vault Name
rds-vault
Central Backup Account ID
12-digit account ID
Backup Plan Name
rds-backup-plan
Backup Plan Schedule Expression
cron(0 0/4 ? * * *), which creates a snapshot every 4 hours. Refer to Cron Expressions for more information.
Backup Resource Condition Key
backup-plan, which is the name of tag to be used for RDS databases to be backed up by the plan.
Backup Resource Condition Value
rds-backup-plan
Delete after days for local vault
7, which is retention in days for snapshots created in the Production account.
Delete after days for cross-account vault
35, which is retention in days for snapshots in the Central Backup account.
IAM user, IAM role or account root that gets permissions to manage the AWS KMS key
role/examplerole
Choose Next.
Choose Next again.
Select the check box to acknowledge resource creation.
Choose Create stack.
When the CloudFormation stack status changes to CREATE_COMPLETE, navigate to the Resources tab and validate that all the resources have been created successfully.
Run the CloudFormation stack in the Central Backup account (Region A)
In this section, you deploy a CloudFormation stack in the Central Backup account in Region A, which is the same Region you chose in your Production account. The stack creates the following resources:
IAM role required by AWS Backup
AWS Backup vault and KMS CMK for vault encryption
Lambda function
EventBridge rule
Sign in to the console in the Central Backup account.
Confirm the Region you’re working in is the same as where you ran the CloudFormation stack in the production account.
Search for CloudFormation or, on the Services menu, choose CloudFormation under Management & Governance.
On the Create stack menu, choose With new resources.
For Template source, select Upload a template file.
Choose Choose file and upload account_b_region_a.yml from the files you downloaded.
Choose Next.
Under Specify stack details, provide a value for each parameter listed in the following table.
Parameter Name
Value Example
Stack Name
aws-backup-rds-stack
AWS Backup IAM Role Name
aws-backup-role
AWS Backup Vault Name
rds-vault
AWS Organization ID
Unique ID of the organization
AWS Backup Destination Region
Select the Region on the drop-down menu where you want the backups to be copied to. This should be a Region different than the Region (Region A) where you’re deploying the current stack.
IAM user, IAM role or account root that gets permissions to manage the AWS KMS key
role/examplerole
Choose Next.
Choose Next again.
Select the check box to acknowledge that the template creates IAM resources.
Choose Create stack.
When the CloudFormation stack status changes to CREATE_COMPLETE, navigate to the Resources tab and validate that all the resources have been created successfully.
Run the CloudFormation stack in the Central Backup account (Region B)
In this section, you deploy a CloudFormation stack in the Central Backup account in Region B. The stack creates the AWS Backup vault and KMS CMK for vault encryption.
Switch to the Region that you want the backup jobs to be copied to.
On the Create stack menu, choose With new resources.
For Template source, select Upload a template file.
Choose Choose file and upload account_b_region_b.yml from the files you downloaded.
Choose Next.
Under Specify stack details, provide a value for each parameter listed in the following table.
Parameter Name
Value Example
Stack Name
aws-backup-rds-stack
AWS Backup Vault Name
rds-vault
AWS Organization ID
Unique ID of the organization
Choose Next.
Choose Next again.
Select the check box to acknowledge that the template creates IAM resources.
Choose Create stack.
When the CloudFormation stack status changes to CREATE_COMPLETE, navigate to the Resources tab and validate that all the resources have been created successfully.
Add resources to the backup plan
In this step, we add resources to our backup plan. Specifically, we add a tag specifying the values you specified for the backup resource condition key and backup resource condition value when running the CloudFormation stack in the Production account.
Sign in to the console with the Production account.
Confirm you’re in the same Region where you deployed the CloudFormation stack (Region A).
Search for RDS or, on the Services menu, choose RDS under Databases.
Choose the RDS database instance you want to back up and choose the Tags tab.
Choose Add tag.
For Tag key, enter backup-plan.
For Value, enter rds-backup-plan.
Choose Add.
Your tag is now listed on the database details.
Validate the backups
The following steps help validate the backups have been created and copied successfully.
Sign in to the console in your Production account.
On the AWS Backup console, choose Backup vaults.
Choose the vault created by the CloudFormation stack.
The following screenshot shows backups of the resources that you added to the backup plan by specifying appropriate tags.
If you used the default values for specifying the cron expression when deploying the CloudFormation stack, a snapshot is taken every 4 hours. In addition, the backup rule created by the stack sets the backup job to start within an hour and complete within 4 hours. You can verify the setting by choosing Backup plans in the navigation pane. Choose the backup plan created by the template and choose the backup rule. The backup job may take some time to complete, and a snapshot appears in the backup vault when it’s done.
Repeat the steps in the Central Backup account in both Regions to validate cross-account and cross-Region backup copies are successfully completed.
The following screenshot shows the Central Backup account in Region A.
The following screenshot shows the Central Backup account in Region B.
Restore the database in the Central Backup account
To restore the database in the Central Backup account, complete the following steps:
Sign in to the console with your Central Backup account.
Choose the Region where the snapshots to be restored are available.
On the AWS Backup console, choose Backup vaults in the navigation pane.
Choose the vault you created with the CloudFormation template.
Select one of the available snapshots.
On the Actions menu, choose Restore.
For DB instance identifier, enter the name for your restored DB instance.
For Restore role, we recommend creating a separate role for this operation with the AWSBackupServiceRolePolicyForRestoresAWS managed policy.
For more information about managed policies, see Managed policies for AWS Backup.
Choose Restore backup.
You can monitor the progress of the job by choosing the Restore jobs tab. Wait until the status of the job changes to Completed.
At this point, a new RDS database instance has been created in the Region you chose. You can verify this by navigating to the Databases page on the Amazon RDS console.
Clean up resources
To remove all the components created by this solution and avoid future charges, complete the following steps:
Sign in to the console with your Production account.
Choose the Region where your RDS database resides.
On the AWS Backup console, choose Backup Vaults and choose the vault created by the CloudFormation template.
Select all the recovery points in the vault and on the Actions menu, choose Delete.
Confirm you choose to delete the snapshots by entering delete and choose Delete recovery points.
Sign in to the console with your Central Backup account.
Repeat steps 2 – 5 in the regions where the Backup Vaults were created.
In each of the accounts and Regions where the CloudFormation stacks were deployed, on the CloudFormation console, select the stack to delete, then choose Delete.
Conclusion
In this post, we demonstrated how to use AWS Backup to automate copying your RDS database snapshots from one account to another in the same Region as well as a different Region. We also looked at how we can restore the database using one of the cross-account snapshots.
Although we discussed backing up and restoring an RDS for Oracle database in this post, you can use the same solution for backing up other RDS database engines as well. You can copy database snapshots between accounts and retain the backups for longer periods to meet regulatory compliance requirements or as a means to further protect your organization from ransomware attacks. You can also set up similar solutions to facilitate restoring copies of your production database in a separate account for development or testing purposes.
To learn more about AWS Backup, refer to the AWS Backup documentation.
If you have any comments or questions, don’t hesitate to leave them in the comments section.
About the Author
Enrique Ramirez is a Senior Cloud Infrastructure Architect at AWS ProServe. In his role, Enrique helps customers through their cloud journey by designing, developing, and implementing cloud-based applications and services.
Read MoreAWS Database Blog