Monitoring microservices in the cloud has become an increasingly cumbersome exercise for teams struggling to keep pace with developers’ rapid application release velocity. One way to make things easier for overloaded security teams is to use the open-source runtime security platform Falco to quickly identify suspicious behavior in Linux containers and applications. The overarching goal of Falco is to uncomplicate visibility in rapidly-deployed, cloud-first workloads everywhere, making life less stressful for your engineering organization.
Falco can help with other vital security tasks, too. You can use it with Google Kubernetes Engine (GKE), for example, to monitor cluster and container workload security. Like a Swiss army knife, Falco can detect abnormal behavior in all types of cloud-first workloads. Its plugin architecture can be used to monitor almost anything that emits a data stream in a known format, including a wide array of Google Cloud services.
Let’s examine how Falco and the gcpaudit plugin enables runtime security monitoring across a wide range of Google Cloud services.
Before we go much further, it’s important to understand the plugin model. Falco’s plugins are shared libraries that conform to a documented API, hooking into Falco’s core functionality. You can use this model to add new event sources, define new fields to be extracted from events, parse content extracted from a data stream, and inject events asynchronously in a given data stream. Officially maintained Falco plugins can be found in its plugin registry.
How the gcpaudit plugin can help analyze log data
The gcpaudit plugin ingests audit logs for several key Google Cloud services, including:
Compute EngineKMSCloud Armor WAFIAMCloud StorageBigQueryCloud SQLPub/SubCloud LoggingCloud Functions
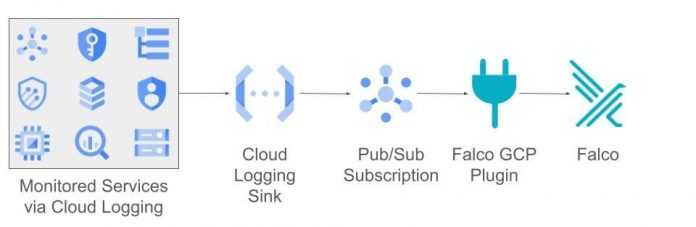
This plugin uses an optimized Google Cloud logging filter or “sink” to send the most critical events from a monitored service to a Pub/Sub topic running within an organization’s project. The gcpaudit plugin acquires events from thePub/Sub topic, applies filters and enrichment (using custom metadata) which operators can then access in Falco.
This filtering process is based on a set of custom Falco rules authored with the MITRE ATT&CK framework in mind. For example, when an action, such as deleting a virtual machine (VM) or removing a database backup, triggers one of these rules, Falco sends out an alert. The plugin provides a centralized view of security events across multiple Google Cloud services and can help detect unauthorized access, data exfiltration, and other types of malicious activity.
To support your other security operations processes, such as building playbooks, event correlation, and triaging incidents, these alerts can then be sent to a security information and event management (SIEM) system such as Chronicle Security Operations. Falco sends alerts to stdout, syslog, an HTTP/HTTPS client or gRPC endpoint by default, but you can leverage a companion project, FalcoSidekick, to send alerts to other destinations in your environment.
There are some important factors to consider with Falco. First, you can’t use Falco on GKE clusters running in Autopilot mode, as it requires privileged access to install its driver. To avoid duplication, only one instance of the gcpaudit plugin should be deployed per monitored environment. For example, you wouldn’t install the plugin on each node in a GKE cluster. Cloud Logging aggregates alerts for a set of monitored services, then forwards to the plugin. The plugin can be installed directly into a compute instance VM, or it can be run as a pod in GKE.
With over 60 outputs such as messaging applications, observability tools, object stores, and databases, you have many options. Since Falco’s an open source project, you can contribute your own outputs, too.
Microservices can be complex, and it can be difficult to ensure alerts get to the right team early enough to have a meaningful impact. Getting the necessary visibility required to secure them can be a challenge, especially when using Kubernetes. By taking advantage of the gcpaudit plugin, security teams can more quickly identify events and respond to incidents in these Google Cloud workloads and improve their organization’s security posture.
To get started and help make your applications “secure every second,” you can try out Falco’s gcpaudit plugin with this detailed walkthrough.
Cloud BlogRead More