We’re continually working to improve Google Cloud’s Identity and Access Management (IAM) capabilities to help secure and govern your cloud environment. When organizations need to grant external applications permission to access Google Cloud APIs and resources there are several options. While many customers have embraced our updated guidance for authentication that includes using Workload identity federation where possible, service account keys are still widely used for authenticating external apps.
To help address security challenges that may arise from the use of service account keys, we are excited to introduce service account key expiry. With this capability, customers can now configure an Organization Policy at the organization, folder, and project level to limit the usable duration of new service account keys.
As companies run applications in Google Cloud, they rely on service accounts for day-to-day operations. These service accounts often have more privileged access than end-user identities, and provide access to workloads and applications in production environments. To help ensure operations are not interrupted, Google Cloud service account keys by default do not expire.
However, not all environments or workloads require a long key lifetime, and key leakage is similar to a password leak — anyone in possession of the key has access to the services and APIs it is authorized to access. Because use of service keys is so prevalent, developers often embed security keys in source code.
If this code is inadvertently uploaded to public repositories, anyone who comes across the key can have access to the cloud resources it’s associated with — a significant security issue. This is where service account key expiry can help, said Antoine Castex, platform architect at L’Oreal: “We are using the new service account key expiry capability in Google Cloud, and it is helping us keep our projects and resources safe. This capability allows us to easily configure an expiration time for service account keys, significantly reducing risks around leaked and compromised keys,” said Antoine Castex.
Service account keys in production environments
Service account key expiry can significantly improve the security posture of any organization using account keys. However, because developers are so used to long-lived keys, changing the default configuration to include expiry can lead to unintended outages that can be difficult to troubleshoot.
Because of this, we recommend using this feature in certain scenarios such as when developers are building code in a non-production environment for an application that can only authenticate with service account keys or using a 3rd party tool that can only authenticate with service account keys. For more advanced organizations that have service account keys disabled already using Organization Policy, this feature can also act as an exception process to allow usage of keys for a limited time without changing their organization’s security policy.
If you want to set up key rotation for your service account keys in your organization, we recommend you monitor keys using cloud asset inventory instead of using key expiry to avoid potential outages. This will allow you to send warning notifications to developers when a key is about to expire and it is time to rotate the key. Alternatively, you can consider embedding the key rotation process into the developer’s workflow by leveraging tools like HashiCorp Vault.
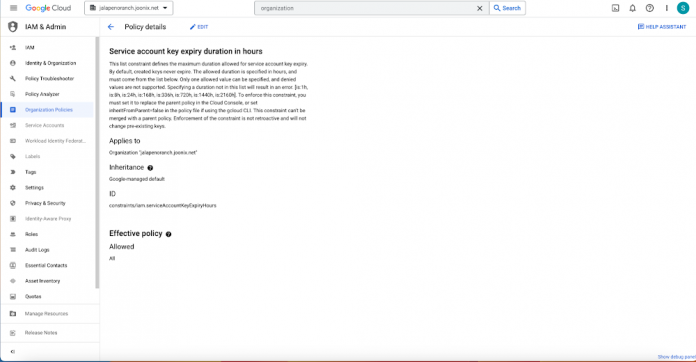
How to setup Service Account Key Expiry
Setting up key expiry is straightforward. As an organization administrator, you can go to the organization policy page and find the constraint with the ID “constraints/iam.serviceAccountKeyExpiryHours”.
You can then click “Edit” and configure a custom allow policy for a duration of (8h, 24h, 168h, 336h, 720h, 1440h, or 2160h) with policy enforcement set to “Replace”. Once this is configured, all new service account keys under the organization/folder/project will use this expiration period.
How to get started
You can get started using the service account key documentation. To learn more about service accounts you can watch this video primer and refer to our Service Accounts overview guide.
Cloud BlogRead More