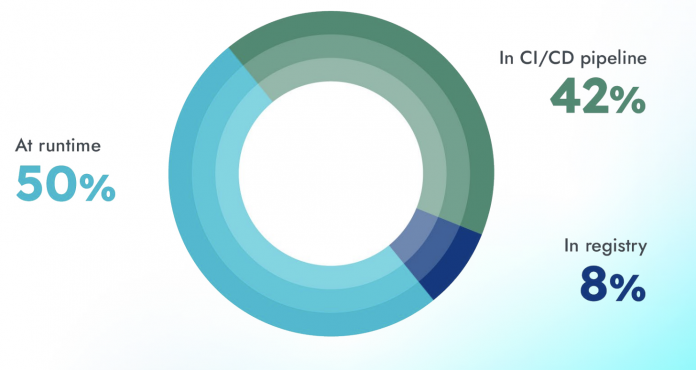
Detecting vulnerabilities in open-source software requires a holistic approach, and security best practices recommend scanning early and often throughout your development lifecycle to help maintain an effective security posture. However, only scanning in the CI/CD pipeline or registry can miss artifacts and containers that are deployed to production through other mechanisms. Likewise, only scanning runtimes can pass over software supply chain vulnerabilities.
To address these security concerns, Artifact Analysis in partnership with Google Kubernetes Engine (GKE) is introducing a new offering called Advanced Vulnerability Insights in public preview. We’re also expanding scanning language support for Artifact Registry.
Figure 1 shows % of containers that are scanned in CICD pipelines, registries, or runtimes. Source data for illustrations in this blog comes from the Sysdig 2023 Cloud-Native Security and Usage Report.
Advanced Vulnerability Insights provides scanning and vulnerability detection in Java, Go, Javascript, and Python language packages. It’s built into our GKE security posture dashboard, and can be enabled on a per-cluster basis. Vulnerability results can be viewed in the Security Posture dashboard and in the Concerns tab along with operating system (OS) concerns, misconfigurations, and security bulletins.
GKE Security Posture can provide customers with a built-in security layer to observe security risks associated with their workloads. You must opt-in to clusters to see vulnerability results. During public Preview there will be no charge to customers, but once Advanced Vulnerability Insights is generally available, there will be a $0.04 per cluster-hour fee. GKE Enterprise customers can enable Advanced Vulnerability Insights at no additional cost, as it’s included in GKE Enterprise entitlement.
Figure 2 shows the types and % of vulnerabilities detected at runtimes.
Beyond OS scanning
More than half the vulnerabilities detected in runtimes are discovered in language packages, according to the Sysdig 2023 Cloud-Native Security and Usage Report. This means that if you’re only scanning for OS vulnerabilities, you may be missing the majority of relevant vulnerabilities.
Figure 3 shows enabling Advanced Vulnerability Insights in GKE security posture.
Figure 4 shows viewing language package vulnerabilities in GKE security posture.
Customers who are already familiar with GKE Security Posture will appreciate how AVI results are incorporated into the Concerns tab. Language vulnerabilities will appear in the same context as OS vulnerabilities, and allow customers to view and prioritize in a single view.
For customers who want to further enhance their security posture, GKE Organizational Policies can be used to enforce that Advanced Vulnerability Insights is enabled on all new clusters, by project or by fleet. Enabling language package scanning by default helps increase the chances of discovering vulnerabilities before an attacker figures out how to exploit it. You can learn more about Custom Organization Policies for GKE, or enable it now.
More for Artifact Registry Customers
Besides new vulnerability detection in GKE, Artifact Analysis still offers built-in support for Artifact Registry. Today, we’re announcing that support for Javascript and Python language packages is generally available. Our registry scanning now supports Java, Go, Javascript, and Python — the same languages we support as part of Advanced Vulnerability Insights.
Enabling Artifact Analysis scanning in Artifact Registry can be an easy and effective way to “shift down” security and begin understanding risk earlier in your development lifecycle. Once you enable the Container Scanning API, any Javascript or Python language package, vulnerabilities that have been discovered will be displayed alongside existing, detected vulnerabilities. Artifact Analysis customers can now scan containers in Artifact Registry and GKE Runtimes to help detect open-source software vulnerabilities across a consistent group of OS and language packages.
Get started today
Enable AVI on your GKE clusters to enjoy the benefits of language package scanning. Learn more about managing your Kubernetes Security Posture.
For Artifact Registry customers enable the container scanning API to begin scanning for OS and language packages vulnerabilities.
Cloud BlogRead More