One benefit of cloud migration is having access to managed services, which can reduce operational overhead. For organizations operating in Microsoft-centered environments, Google Cloud offers a highly-available, hardened Managed Service for Microsoft Active Directory running on Windows virtual machines. Managed Microsoft AD provides benefits such as automated AD server updates, maintenance, default security configurations, and needs no hardware management or patching.
Most organizations adopting Managed Microsoft AD will be migrating from an existing on-premises AD deployment. Typically, when migrating Active Directory objects, existing users cannot continue to access resources in the new domain unless security identifier (SID) history is preserved. This can lead to additional work for administrators as the permissions need to be recreated post migration.
To make migrations more seamless and eliminate extra effort, we are excited to announce a new capability in Managed Microsoft AD: support for the migration of AD users with SID history, now available in Preview. Now, users can retain historic Access Control List (ACL) entries so that users can access resources without having to recreate resource permissions post-migration.
Steps to migrate on-premises AD users to Managed Microsoft AD
To get started, you can use Active Directory Migration Tool (ADMT) to migrate an on-premises AD domain to Managed Microsoft AD specifically with SID history.
1. Prepare your on-premises Active Directory and Managed Microsoft AD
As a prerequisite for migration, users need to set up a two-way trust between existing on-premises AD domain and new Managed Microsoft AD domain.
Either a single user or a team within the users’ organization can perform the migration activities. When a team is involved, we recommend adding the team members to a domain local group in Managed Microsoft AD. Users can connect to a Managed Microsoft AD domain and use the standard Active Directory tools such as Active Directory Users and Computers (ADUC) that is part of RSAT: Active Directory Domain Services for adding those users to the domain local group. Remember that users need to add this domain local group to the pre-created groups in Managed Microsoft AD, after enabling permissions as described in step 3.
2. Prepare a Google Compute Engine Virtual Machine and set up ADMT
As a next step, install and set up Microsoft Active Directory Migration Tool (ADMT) and Microsoft SQL Server 2016 Express on a Google Compute Engine Virtual Machine. You need to make sure that this VM is not a domain controller and then join the VM to Google Cloud Managed Microsoft AD domain.
3. Enable permissions on Managed Microsoft AD
After users prepare the on-premises Active Directory and Managed Microsoft AD, they can enable the required permissions in Managed Microsoft AD to migrate the users with SID History. You can use the following gCloud CLI command:
After users enable the permissions, add the domain local group to the “Cloud Service Administrators” and “Cloud Service Migrate SID Administrators” (these groups are pre-created in Managed Microsoft AD) so that the designated users will have the required permissions for Active Directory migration with SID history.
For more information, see Enable permissions for migrating an on-premises domain with SID history and also ensure you understand these security implications.
4. Configure ADMT and install PES service
To migrate passwords securely during the domain migration, users need to use the Microsoft Password Export Server (PES) service. Before users install PES on the on-premises domain, create the encryption key on the VM running ADMT. Users can use the following command to create the encryption key:
It creates and stores the encryption key at the location specified at KEY_FILE_PATH. You can copy the encryption key to the local drive of the on-premises domain controller where you have installed the PES service.
Note: It is recommended to run the PES service only when you migrate passwords.
5. Migrate AD users to Google Cloud Managed Microsoft AD
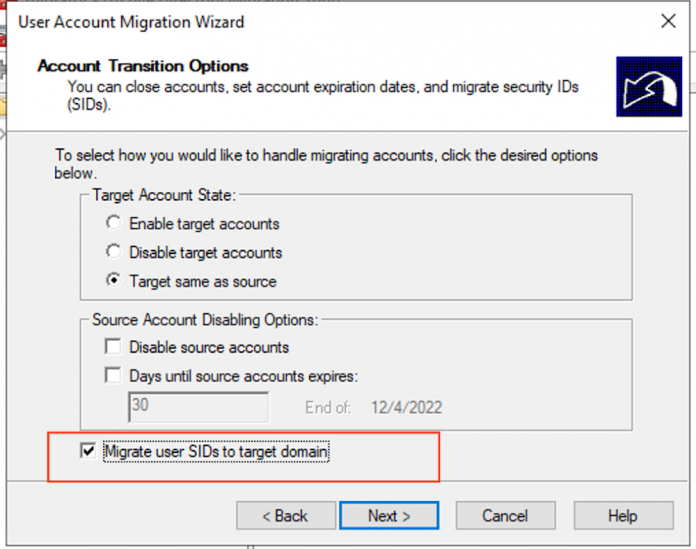
Now that users have the environment ready and the required permissions enabled, migrate the AD users & groups along with the SID history. Users will have to use the User Account Migration Wizard in the ADMT tool. For detailed steps, please refer to the ADMT guide. In this wizard, select the “Migrate user SIDs to target domain” option on the Account Transition Options page.
Note: You may want to migrate other AD objects as well, so as a best practice, we recommend that you maintain a migration checklist and verify managed objects in the checklist post-migration.
The migration process window will show the status of how many users, groups and computers have been migrated. You can click on “View Log” to examine the migration logs for errors and check the details of the operations.
After the migration process is completed, verify that the users exist in the Managed Microsoft AD domain using the Active Directory Users and Computers tool. Users can also use the AD login to verify that the access is set up correctly and verify that users can login successfully with resource permissions based on the SID history.
Now users have successfully migrated AD objects including users along with SID history from on-premises AD domain to a new Managed Microsoft AD domain. After successful migration, we recommend disabling the user permissions that was enabled for migration.
Next Steps
We are continually evolving our Managed Microsoft AD features to help you more easily and effectively manage AD tasks. Here are additional resources where you can learn more about Managed Microsoft AD and these new features.
Managed Service for Microsoft AD documentationExisting domain migration overviewEnable permissions for migrating an on-premises domain with SID history
Cloud BlogRead More