Amazon RDS Proxy is a fully managed, highly available database proxy for Amazon Relational Database Service (Amazon RDS) that makes applications more scalable, more resilient to database failures, and more secure. With RDS Proxy, you can handle unpredictable surges in database traffic that might otherwise cause issues due to oversubscribing connections or creating new connections at a fast rate.
Security best practices recommend placing your databases and proxies inside a private network with no internet inbound access. However, software as a service (SaaS) providers and third-party integrations often rely on secure communications over the internet.
In this post, we show you how to securely and efficiently connect external applications to a single RDS instance or Amazon Aurora cluster using AWS Secrets Manager, RDS Proxy, Network Load Balancer, TLS/SSL Certificates, and Amazon Virtual Private Cloud (Amazon VPC); configuring Security Groups and Network access control lists (ACLs); and optionally using AWS Shield to protect against DDoS attacks.
Solution overview
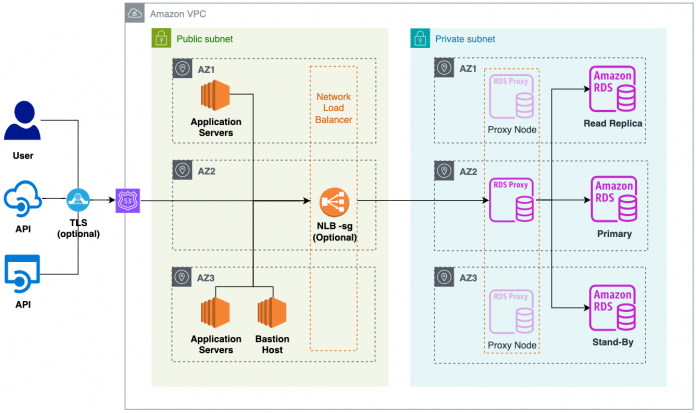
For our solution, we have an RDS instance configured with Multi-AZ and one read replica (optional) residing on a private subnet. Connections to this instance are managed via RDS Proxy, which resides on the same subnet as the database instance. To make RDS Proxy accessible via the internet, we use a Network Load Balancer located on the public subnet to provide a URL endpoint used to connect to the database. To secure the solution, we use network Access Control Lists (ACLs) to restrict access in and out of the VPC, and security groups to act as a firewall for RDS Proxy and the RDS instance. Optionally, Shield is available to protect against DDoS attacks. SSL/TLS connections are also recommended to provide another layer of security by encrypting data that moves between your client and a DB instance.
The following diagram illustrates the solution architecture.
This solution opens RDS Proxy connectivity through the internet; for security, we recommend testing on an isolated VPC or sandbox environment to avoid accidental exposure.
Prerequisites
This sample solution requires that you have a set of networking resources in place, such as the following:
A VPC
A database security group
A bastion host (jump box) and pgAdmin admin
An RDS or Amazon Aurora for PostgreSQL instance
pgAdmin or your preferred tool on your desktop
After all the prerequisites are met, you are ready to configure RDS Proxy for external access.
Create a database user with appropriate privileges
Create a new database user with the following steps:
Connect to your bastion host (jump box).
Connect to the database using pgAdmin or the tool of your choice.
From pgAdmin, open a new query with the Query Tool or tool of your choice.
Use the following code to create a read/write database user and grant limited privileges to the user within the database:
Create a Secrets Manager secret
RDS Proxy uses secrets to validate and connect to the database. Complete the following steps to create a new secret:
On the Secrets Manager console, choose Secrets in the navigation pane.
Choose Store a new secret.
For Secret Type, select Credentials for Amazon RDS database.
For Username, enter rdsproxy_rwuser (your database user).
For Password, enter your password for rdsproxy_rwuser.
For Encryption key, choose aws/secretsmanager.
For Database, select postgresql-02 (your database instance).
Choose Next.
For Secret name, enter rdsproxy_rwuser.
For Description, enter an optional description.
Choose Next.
Rotation schedule, specify a schedule (optional).
Choose Next.
Review your options and choose Store.
Create a proxy
To create a proxy, complete the following steps:
On the Amazon RDS console, choose Proxies in the navigation pane.
Choose Create proxy.
For Engine family, choose PostgreSQL.
For Proxy identifier, enter rdsproxy-postgresql02.
Set Idle client connection timeout to 30 minutes.
For Target group configuration, choose postgresql02.
Under Authentication, specify the following:
For Identity and access manager (IAM) role, choose Create IAM role.
For Secret Manager secrets, choose rdsproxy_rwuser.
For Client authentication type, choose SCRAM SHA 256.
For IAM authentication, select Not Allowed.
Under Connectivity, specify the following:
Optionally, choose Require Transport Layer Security (TLS).
For Subnets, choose the same subnets as the database subnet group.
Under Additional connectivity configuration, specify the following:
For VPC, choose your VPC.
Existing VPC security groups, choose database_security_group.
Choose Create proxy.
You also need to obtain your RDS Proxy IP addresses.
Go to your EC2 bastion host (jump box).
Open a terminal or command line perform a nslookup against your RDS Proxy (for example, nslookup rdsproxy-postgresql02.proxy-xxxxxxxxxxxx.us-east-1.rds.amazonaws.com).
Save the IP addresses for later use.
Create a Network Load Balancer
To create a Network Load Balancer, complete the following steps:
On the Amazon EC2 console, choose Target groups in the navigation pane.
Choose Create target group.
Under Basic configuration, specify the following:
For Target type, select IP addresses.
For Target group name, enter rds-proxy-postgresql01-tg.
For Protocol, choose TCP.
For Port, enter 5432.
For IP address type, choose IPv4.
For VPC, choose your VPC.
For Health check protocol, choose TCP.
Choose Next.
On the Register targets page, for Choose a network, choose your target VPC.
Specify the IP addresses and define the ports (repeat for every RDS Proxy IP):
For IPV4 addresses, enter your RDS Proxy IP addresses.
For Port, enter 5432.
Select Include as pending below.
On the Review targets page, for Targets, choose All.
Choose Create target group.
Under Add listener, specify the following:
For Protocol, choose TCP.
For Port, enter 5432.
For Default action, choose rds-proxy-postgresql01-tg.
Choose Add.
On the Network mapping tab, note down the CIDR range for the load balancer. You will need this for next step.
Update your network ACL
Complete the following steps to update your network ACL:
On the Amazon VPC console, choose Network ACLs in the navigation pane.
For Network ACL, choose <<Network ACL of your VPC>>.
On the Inbound rules tab, choose Edit inbound rules, and Add rule.
Add the following rules:
Inbound rule 1:
For Type, choose All Traffic.
For Source, enter your public IP (for example, 99.5.5.5/32).
Inbound rule 2:
For Type, choose All Traffic.
For Source, enter the internal IPv4 CIDR range for the subnet groups that require access to RDS Proxy (for example, 10.0.0.0/16).
Inbound rule 3 (if not using Amazon Route 53):
For Type, choose HTTP (80).
For Source, enter 0.0.0.0/0.
Inbound rule 4 (if not using Route 53):
For Type, choose HTTPS (443).
For Source, enter 0.0.0.0/0.
Update your security group
Complete the following steps to update your security group:
On the Amazon VPC console, choose Security groups in the navigation pane.
Choose the security group database_security_group.
On the Inbound rules tab, choose Edit inbound rules, and Add rule.
Add the following rules:
Inbound rule 1:
For Type, choose PostgreSQL.
For Source, choose your database security group (sg-xxxxxxxxx).
Inbound rule 2:
For Type, choose PostgreSQL.
For Source, enter the network load balancer IP range (for example, 10.0.0.0/20).
For Description, enter Internal IP AZ1 Network Load Balancer.
Inbound rule 3:
For Type, choose PostgreSQL.
For Source, enter the network load balancer IP range (for example, 10.0.16.0/20).
For Description, enter Internal IP AZ2 Network Load Balancer.
Continue adding inbound rules as needed for your IP addresses.
Test connectivity
From an authorized desktop (allowed IP range on network ACL), launch pgAdmin (or your tool of choice) and open a new query. Connect to the RDS instance using the Network Load Balancer endpoint as the host name, and the database user and password configured for RDS Proxy.
To encrypt your connection, follow using SSL/TLS to encrypt a connection to a DB instance.
Note:
In this solution, using SSL mode: verify full or requiring hostname validation will cause the validation to fail.
Clean up
To avoid incurring future charges, delete any resources that you created as part of this post, such as the following:
VPC
Database security group
Database subnet group
Bastion host (jump box)
RDS for PostgreSQL or Aurora PostgreSQL instance
RDS Proxy
Network Load Balancer
pgAdmin or the tool you installed to query the database
Conclusion
This post showed how to securely and efficiently connect external applications to a single RDS instance using RDS Proxy.
Workloads experiencing hundreds or thousands of internet-routed concurrent connections can benefit from such an architecture. This solution can help sustain seasonal highs and unpredictable increases in workload.
To learn more about where or when to use RDS Proxy, check out Planning where to use RDS Proxy.
About the Authors
Jose A. Ramirez is a Database Specialist Solutions Architect at AWS. He has over 25 years of experience in the technology industry as a DBA and Systems Administrator. Jose now focuses on architecting solutions for customers looking to modernize their applications and databases in AWS.
John Scott is a Database Specialist Solutions Architect based in Atlanta. He has years of experience as a Linux Admin and DBA for companies of all sizes. John’s favorite things are family, great barbecue, and Amazon Aurora.
Archana Sharma is a Sr. Database Specialist Solutions Architect, working with Worldwide Public Sector customers. She has years of experience in relational databases, and is passionate about helping customers in their journey to the AWS Cloud with a focus on database migration and modernization.
Read MoreAWS Database Blog