At Google Cloud, we’re driven by a vision of invisible security, where advanced security capabilities are engineered into our platforms, operations are simplified, and stronger security outcomes can be achieved. As we pursue this ideal, we want to help make security easier to use and manage. Our new built-in Google Kubernetes Engine (GKE) security posture dashboard (now available in Preview) does both, with opinionated guidance for customers that can help improve the security posture of your GKE clusters and containerized workloads. It also includes insights into vulnerabilities and workload configuration checks, and offers integrated event logging so you can subscribe to alerts and stream insight data elsewhere.
Expanding security coverage to your workloads
While a move to Kubernetes provides the foundation for application modernization and developer agility that underpins many organizations’ digital transformation efforts, it can also create new security requirements. Many organizations choose GKE to run and secure containerized workloads because it can help with vital security tasks, including:
manage patching, hardening, and compliance;
enforce security best practices;
and provide powerful controls for segmentation and isolation.
In addition to infrastructure security, containerized workload security is also important. When moving to Kubernetes (or any new platform or architecture,) the threat models, controls, and best practices might not be immediately clear or obvious. Moving to Kubernetes is often part of the digital transformation process for many organizations, and organizations wish to avoid speed bumps that slow modernization and innovation. This process can often lead teams new to Kubernetes to consider expensive and complex third-party tooling that they may not need.
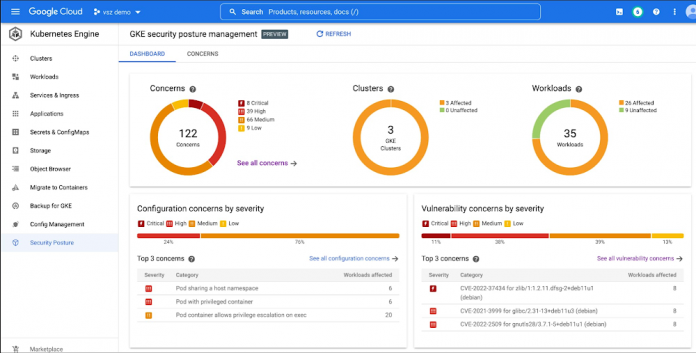
GKE security posture management can enhance the visibility of workload security, delivering “out-of-the-box” foundational security tools that can simplify management, and can help reduce the need for specialized security expertise. We’re now providing these tools at no extra cost to GKE customers.
Container security made simple
GKE leverages industry standards and the GKE team’s security expertise to provide detailed assessments and assign severity ratings. The dashboard can also show you which of your workloads are affected by a specific security concern, and can make suggestions on how to fix the problem.
Workload vulnerability awareness
If you’re drowning in a sea of Common Vulnerabilities and Exposures (CVE) alerts that seem disconnected from your critical workloads, you are not alone. To address this, GKE scans all of your workloads for CVEs in the Operating System at no extra charge every single day, bubbling the most potentially impactful vulnerabilities to the top of the dashboard. These vulnerability findings are mapped directly to your running workloads, with filters and sorting that can help make prioritization and remediation a breeze.
Of course, we also encourage you to “shift-left” and scan for vulnerabilities before you deploy to GKE using tools like Container Analysis, which can automatically scan vulnerabilities in images pushed to Artifact Registry and Container Registry. Implementing vulnerability assessment at runtime can help to highlight the potential impact of newly discovered vulnerabilities.
Workload security misconfiguration awareness
An overly permissive Kubernetes configuration can threaten the overall security of your clusters. The GKE team and industry experts have worked to develop configuration security standards such as the Pod Security Standards. These specifications can help you avoid issues such as running overly-privileged users and unintended host node access.
However, it’s not always easy to ensure that your workloads comply with these standards. The security posture dashboard can provide continuous analysis of deployed workload configurations to surface potentially overly permissive configurations and provide you with specific, actionable fixes.
Used together with policy enforcement tools like Policy Controller, GKE now can provide comprehensive enforcement and awareness tools to help prevent and detect misconfigured workloads.
Get started today
GKE Autopilot already provides a managed Kubernetes experience that can reduce technical expertise barriers with an opinionated, “hands-free” operating mode. GKE now extends this managed experience to the security domain with an opinionated set of standards-based guardrails and integral security tools.
Learn more about our managed platform for containerized applications, which can provide a powerful and flexible Kubernetes experience.
Cloud BlogRead More