Customers within a variety of industries (healthcare and life sciences, financial services, and retail, among others) require a stronger security posture. Particularly, if the databases being hosted contain sensitive data such as credit card numbers or national identification numbers (for example, US Social Security numbers), providing a solution that allows you to encrypt this data and control access to database administrators becomes crucial. Always Encrypted is Microsoft SQL Server’s answer to this security requirement.
Always Encrypted allows clients to encrypt sensitive data inside client applications and never reveal the encryption keys to the database engine. This provides a separation between those who own the data and can view it, and those who manage the data but shouldn’t have access: database administrators, cloud database operators, or other high-privileged unauthorized users. As a result, Always Encrypted enables you to confidently store your sensitive data in the cloud, and to reduce the likelihood of data theft by malicious insiders. Always Encrypted makes encryption transparent to applications. An Always Encrypted-enabled driver installed on the client computer achieves this by automatically encrypting and decrypting sensitive data in the client application. The driver encrypts the data in sensitive columns before passing the data to the database engine, and automatically rewrites queries so that the semantics to the application are preserved. Similarly, the driver transparently decrypts data, stored in encrypted database columns, contained in query results.
In this post, we provide you with step-by-step instructions on how to set up Always Encrypted on an Amazon Relational Database Service (Amazon RDS) for SQL Server instance using the Windows Certificate Store. Other key stores available for Always Encrypted (Azure Key Vault, Hardware Security Module) are not supported as of this writing.
Prerequisites
To set up this solution, you need a working environment with the following resources:
Development host with SQL Server installed (Windows device where the Always Encrypted Certificate will be generated).
Target application server running Windows and hosted on Amazon Elastic Compute Cloud (Amazon EC2).
SQL Server 2016 or higher instance (RDS for SQL Server instance).
Amazon Simple Storage Service (Amazon S3) bucket to store the certificate file.
Always Encrypted certificate.
To generate a certificate for the column master key using a local SQL Server instance running on your development machine, complete the following steps:
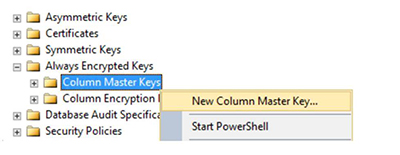
With SQL Server Management Studio (SSMS), open the folder Column Master Keys under the Security node of the database you are planning to encrypt, right-click on the “Column Master Key” folder, and select the “New Column Master Key…” option, as shown.
Store the certificate in the Windows Certificate Store – Current User key store.
Locate the Always Encrypted certificate and take note of the thumbprint (choose the certificate to open the details dialog box) using the Certificates option on the Microsoft Management Console (MMC). You will need this thumbprint for the scripts we develop to automate the process. If you haven’t accessed the Certificates Snap-in before, follow the detailed steps included here.
Open the Microsoft Management Console (MMC).
Navigate to the File Menu and select the option Add or Remove Snap-ins.
Select the Certificates option from the available snap-ins listed.
Navigate to the PersonalCertificates folder.
Double-click on Always Encrypted Certificate.
Select the Details tab, scroll down, and select the Thumbprint property.
Export the certificate to a PFX file by choosing Copy to File, as shown in the following dialog box.
Choose Next on the Certificate Export Wizard dialog box.
Select the option “Yes, export the private key” and then choose Next.
Select the Personal Information Exchange (.PFX) format option and then choose Next.
Type-in a password, select the “AES256-SHA256” encryption option, and then choose Next.
Specify the appropriate path and file name; choose Next.
Choose Finish to complete the certificate export process.
Upload this file to the designated S3 bucket.
Configure Always Encrypted on an RDS for SQL Server instance
Once all pre-requisite steps have been completed and you have been able to successfully export and Always Encrypted certificate to a PSX file, you are ready to configure Always Encrypted on your Amazon RDS for SQL Server instance. In order to do so, complete the following steps:
Connect remotely to the target application server (Windows EC2 client) leveraging Microsoft Remote Desktop Protocol Client (RDP).
Download the PSX file with the certificate from Amazon S3 to a local folder.
Import the certificate into the target application server.
Connect to Amazon RDS for SQL Server using SQL Server Management Studio (SSMS) with the Always Encrypted option enabled as shown below.
Open a new query window and adjust the query options to enable parameterization for Always Encrypted.
Create a new database to host some encrypted data:
Create the column master key, referencing that certificate thumbprint we captured earlier:
Create a column encryption key. One option is to leverage SQL Server Management Studio GUI. In this case, locate the “Column Encryption Keys” folder under the “Always Encrypted Keys” node, right-click on the folder and select the option “New Column Encryption Key…”. Type-in an appropriate name for your column encryption key, select the column master key created above and click “OK”. Alternatively, you can leverage the T-SQL script below. Make sure to adjust the encrypted value of the certificate shown in the following code to match the certificate you are actually using in your environment:
Verify that encryption was properly set up (a sample output is included for your reference):
Create a table with encrypted columns. The following sample includes both options for a column encryption key: deterministic and randomized. In general, the most used option is deterministic because it’s significantly faster, but in some use cases, randomized is the better option (when the cardinality of the column is very low, for example). It is important to note in the T-SQL statement below that for the deterministic encryption option on a string column, a binary-code point collation (_BIN2) is required.
Query the recently created table:
Insert a few records. In this sample, it’s important to keep the insert operations as single statements, otherwise SSMS will throw an error.
Query the table again:
Note that the values are unencrypted. If you run this query from any other client that doesn’t have the certificate deployed, you will only see the encrypted values. A possible test is to remove the certificate from the client and then run the query again.
Conclusion
In this post, we demonstrated how to set up Always Encrypted on an Amazon RDS for SQL Server instance using the Windows Certificate Store. It is important to keep in mind that Microsoft SQL Server Always Encrypted has been released with a number of limitations and they still apply once you have setup this feature on your Amazon RDS for SQL Server instance. Should you not need to use the resources created following along the instructions included in this post, please remember to clean-up your environment: delete the Amazon RDS for SQL Server instance created during the exercise, delete the Amazon S3 bucket used to host the PSX certificate file, and terminate the Amazon EC2 instance used as the target application server (Always Encrypted Client).
If you have any questions, comments, or feedback, please leave them in the comments section of this post.
About the Author
Camilo Leon is a Principal Solutions Architect at AWS specialized on databases and based off San Francisco, California. He works with AWS customers to provide architectural guidance and technical support for the design, deployment and management of their AWS relational database workloads and business applications. In his spare time, he enjoys mountain biking, photography, and movies.
Read MoreAWS Database Blog